| 일 | 월 | 화 | 수 | 목 | 금 | 토 |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | ||
| 6 | 7 | 8 | 9 | 10 | 11 | 12 |
| 13 | 14 | 15 | 16 | 17 | 18 | 19 |
| 20 | 21 | 22 | 23 | 24 | 25 | 26 |
| 27 | 28 | 29 | 30 |
- Python
- 방화벽dmz
- 자바
- Java
- 파이썬
- JavaScript
- 더강
- 독서
- 네트워크dmz
- 오블완
- 책
- 오라클
- 데이터베이스
- 개발
- html
- 갑상선암
- 자바스크립트
- 코딩
- dmz란
- css
- 카페더강
- 유리트리트
- 웹퍼블리싱
- 프로그래밍
- dmz구성
- 홍천유리트리트
- dmz네트워크
- 서평
- database
- 티스토리챌린지
- Today
- Total
JiYoung Dev 🖥
Spring Security 적용기 (1) Spring Security란? 본문
새롭게 프로젝트를 시작하면서 적용해보고 싶었던 기술 중 하나인 Spring Security.
어떠한 기술이며 어떠한 원리를 바탕으로 동작하는지, 그리고 실제 프로젝트에 적용하는 것까지 하나 하나 포스팅해보고자 한다.
이번 포스팅은 Spring Security 적용기의 첫 번째 파트, Spring Security란 무었인지에 대해 이야기해보고자 한다.
목차
1. Spring Security 개념
2. Spring Security 특징
3. Architecture
🤍 Spring Security 개념
Spring Security는 인증, 권한 부여 및 일반적인 공격에 대한 보호를 제공하는 Spring 프레임워크이다.
개발을 할 때 기능 부분에서 가장 먼저 작업하는 부분이 바로 회원가입, 로그인, 로그아웃과 같은 기능일 것이다.
간단해 보이지만 실제 이러한 기능은 사용자 개인정보와 맞닿아 있어 보안, 인가 뿐만 아니라 세션/권한 관리 등 생각해야 할 부분이 많은 부분이다. Spring Security는 Spring 생태계 내에서 개발자들이 보안 관련 기능을 효율적이고 신속하게 구현할 수 있도록 도와준다.
🤍 Spring Security 특징
Spring Security는 인증, 권한 부여 및 일반적인 악용에 대한 보호를 위한 포괄적인 지원을 제공한다.
또한 사용을 단순화하기 위해 다른 라이브러리와의 통합을 제공한다.
1. 인증(Authentication)
인증은 특정 리소스에 엑세스하려는 사람의 신원을 확인하는 방법이다.
사용자를 인증하는 일반적인 방법은 사용자에게 사용자 아이디와 비밀번호를 입력하도록 요구하는 것이다.
2. 권한 부여(Authorization)
1. 요청 기반 권한 부여
2. 메소드 기반 권한 부여
권한 부여란, 특정 리소스에 엑세스 할 수 있는 사람을 결정하는 것이다.
Spring Security는 요청/ 기반 인증과 메소드 기반 인증을 허용한다.
3. 악용으로부터 보호(Protection Against Exploits)
Spring Security는 일반적인 악용에 대한 보호를 제공한다.
여기서 일반적인 악용이란
1. CSRF
2. HTTP 헤더
3. HTTP 요청
위의 3가지를 말한다.
3-1. CSRF(Cross Site Request Forgery) : 크로스 사이트 요청 위조 공격
CSRF는 인증된 사용자가 웹 애플리케이션에 특정 요청을 보내도록 유도하는 공격 행위를 말한다.
CSRF는 생성된 요청이 사용자의 동의를 받았는지 확인할 수 없는 웹 애플리케이션의 취약점을 이용한다.
공격자의 요청이 사용자의 요청인 것처럼 속이는 공격 방식이기 때문에 크로스 사이트 위조 요청이라 한다.
CSRF는 웹 브라우저를 속여 사용자가 로그인한 애플리케이션에서 무단으로 특정 작업을 진행하는 방식으로 이루어진다.
1. 공격자가 특정 은행의 계좌에서 공격자의 계좌로 천만원을 송금하라는 요청을 위조한다.
2. 위조한 요청은 하이퍼링크에 삽입해 이메일로 전송하거나 웹사이트 자체에 삽입한다.
3. 사용자가 공격가 생성한 이메일 하이퍼링크나 웹사이트 링크를 클릭하면 은행에 천만원을 송금하라는 요청이 전송된다.
4. 요청을 받은 은행 서버는 사용자의 요청대로 송금을 진행한다.
위와 같이 CSRF 공격이 가능한 이유는 피해자 웹사이트의 HTTP 요청과 공격자 웹사이트의 요청이 정확히 동일하기 때문이다.
Spring Security는 이러한 위험으로부터 보호를 위해
1. 동기화 장치 토큰 패턴(Synchronizer Token Pattern)
2. 세션 쿠키에 SameSite 속성 지정 방법을 사용한다. (SameSite Attribute)
※ 두 가지 방법 모두 읽기 전용이어야 한다.
동기화 장치 토큰 패턴(Synchronizer Token Pattern)
해당 솔루션은 각 HTTP 요청에 Session, Cookie 외에도 CSRF Token이라는 안전한 무작위 생성값이 HTTP 요청에 있는지 확인하는 것이다. HTTP 요청이 제출되면 서버는 예상되는 CSRF 토큰을 조회하고 이를 HTTP 요청에 담긴 토큰 값과 비교하여 같으면 요청을 수락하고, 다르면 요청을 거부하는 방식이다.
SameSite 속성
해당 솔루션은 웹 브라우저 쿠키 보안과 관련된 속성 중 하나이다. 이 속성은 쿠키를 어떤 상황에서 전송할 것인지 제어한다.
1. Strict : 쿠키는 항상 동일한 출처 요청에서만 전송된다.
2. Lax : 쿠키는 타사 사이트에서의 GET 요청에 대해서만 전송된다.
3. None : 쿠키는 모든 요청에 대해 전송한다. 해당 옵션은 보통 HTTPS 연결에서만 동작하며, Secure 속성이 함께 사용되어야 한다.
4. 통합(Integration)
Spring Security는 수많은 프레임워크 및 API와의 통합을 제공한다.
대표적으로 암호화, 스프링 데이터, Java 동시성 API, Jackson, Localization에 대한 통합을 제공한다.
Cryptography
Spring Security Crypto 모듈은 대칭암호화, 키 생성 및 비밀번호 인코딩을 지원한다.
Spring Data Integration
Spring Security는 쿼리 내에서 현재 사용자를 참조할 수 있는 Spring Data 통합을 제공한다.
Concurrency Support
다중 스레드 환경에서 Spring Security 작업을 위한 낮은 수준의 추상화를 제공한다.
Jaskson Support
Spring Security는 Spring Security 관련 클래스를 유지하기 위해 Jackson 지원을 제공한다.
Localization
인증 실패 및 엑세스 거부와 같은 메시지를 포함하여 모든 예외 메시지를 현지화할 수 있다.
🤍 Architecture
Spring Security의 서블릿 지원은 서블릿 필터를 기반으로 한다.

서블릿 필터(Servlet Filter)란?
Sevlet 실행 전, 후에 어떤 작업을 하고자 할 때 사용하는 것으로 Servlety Container에 등록하여 사용한다.
[서블릿 필터 흐름]
• HTTP 요청 → WAS → Filter → Servlet → Controller
필터를 적용하게 되면 필터가 호출 된 다음 서블릿을 호출한다. 따라서 모든 고객의 요청 로그를 남기는 요구사항이 있다면 필터를 사용하면 된다.
[서블릿 필터 제한]
• HTTP 요청 → WAS → Filter
위의 흐름과 같이 필터에서 적절하지 않은 요청이라 판단하여 서블릿을 호출하지 않을 수도 있다.
이렇게 필터를 사용하여 적절한 요청인지, 적절하지 않은 요청인지 판단해 서블릿을 호출하거나 호출하지 않을 수 있다. 따라서 로그인 여부를 체크하기에 적합하다.
[서블릿 필터 체인]
• HTTP 요청 → WAS → Filter1 → Filter2 → Filter3 → Servlet Filter → Servlet → Controller
필터를 체인하여 다수의 필터를 추가할 수 있다.
1. DelegatingFilterProxy
Spring Security는 사용하고자 하는 FilterChain들을 Servlet Container 기반의 필터 위에서 동작시키기 위해 DelegatingFilterProxy라는 클래스를 이용한다.
Spring Security의 필터들은 스프링 애플리케이션의 일부가 아닌 독립적인 객체로 정의된다. 이를 스프링 애플리케이션 컨텍스트와 통합하기 위해 'DelegatingFilterProxy'가 사용된다. DelegatingFilterProxy는 인증, 인가, 로깅 등 보안 관련 작업을 수행하는 필터 체인을 관리하고, 각 필터가 스프링 애플리케이션 컨텍스트에서 정의된 빈으로 위임할 수 있도록 한다.
즉, DelegatingFilterProxy는 스프링 애플리케이션과 Spring Security 사이의 다리 역할을 한다.

2. FilterChainProxy
FilterChainProxy는 보안 필터들을 관리하여 HTTP 요청의 처리를 담당한다.
각 필터는 특정한 보안 작업을 수행하며, 이러한 필터들은 체인으로 구성된다.
각각의 필터는 요청을 받아들이고, 필요한 작업을 수행한 후 다음 필터로 요청을 전달한다.
이런식으로 필터 체인이 순차적으로 실행되면서 보안 작업이 수행된다.
주요 기능으로 사용자 인증(Authentication), 인가(Authorization), 세션 관리, CSRF 방어, 로깅 등이 있다.
각각의 보안 기능은 하나 이상의 필터로 구현되며, 이러한 필터들을 FilterChainProxy가 관리한다.
Spring Security에서는 여러 개의 FilterChainProxy가 사용될 수 있다. 각각의 FilterChainProxy는 특정한 요청 패턴 또는 보안 수준에 따라 다른 필터 체인을 관리한다. 이를 통해 애플리케이션의 다양한 부분에 대해 서로 다른 보안 구성을 적용할 수 있다.
FilterChainProxy는 일반적으로 스프링 애플리케이션 컨텍스트에서 빈으로 정의된다. 즉, 스프링 IOC 컨테이너에서 관리되고 의존성 주입을 받을 수 있다는 것이다. 그러나 서블릿 컨테이너는 직접적으로 스프링 빈을 인식하지 못한다. 대신 서블릿 컨테이너에서 Filter를 등록하고 관리한다. 즉, 스프링에서 관리되는 FilterChainProxy를 서블릿 컨테이너에 등록하기 위해서는 DelegatingFilterProxy를 사용하여 FilterChainProxy를 등록해야 한다.
결국, FilterChainProxy는 스프링 빈으로 정의되지만, 서블릿 컨테이너에 등록하기 위해 DelegatingFilterProxy로 래핑되어야 한다. 이를 통해 FilterChainProxy는 서블릿 컨테이너의 라이플사이클에 맞게 동작하고 필터 체인을 관리할 수 있다.
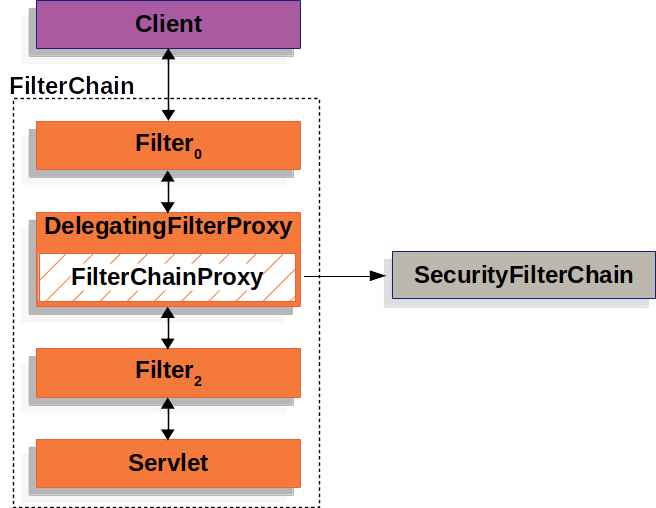
3. SecurityFilterChain
SecurityFilterChain은 현재 요청에 대해 어떤 Spring Security 필터 인스턴스를 호출해야 하는지 결정하기 위해 FilterChainProxy에 의해 사용된다.

SecurityFilterChain에 있는 보안 필터들은 일반적으로 빈으로 정의된다. 그러나 이러한 필터들은 DeligatingFilterProxy 대신 FilterChainProxy에 등록된다.

다중 SecurityFilterChain 그림에서 FilterChainProxy는 어떤 SecurityFilterChain을 사용할 지 결정한다. 일치하는 SecurityFilterChain만 호출된다. 예를들어 /api/messages/ URL이 요청된 경우, /api/** 패턴의 SecurityFilterChain0에 일치하므로 SecurityFilterChain0만 호출된다.
4. Security Filters
실제 인증, 권한 부여과 같은 보안 작업을 수행하는 필터를 말한다. 제공하는 종류로는 인증 필터(Authentication Filter), 인가 필터(Authorization Filter), 세션 관리 필터(Session Management Filter), 로깅 및 모니터링 필터(Logging and Monitoring Filter) 등이 있다.
정리하자면,
스프링 빈으로 등록되는 인증, 인가 등의 작업을 수행하는 Security Filter들이 존재하고, 이러한 Security Filter는 SecurityFilterChain으로 구성된다. SecurityFilterChain은 각 필터의 순서와 구성을 정의한다.
FilterChainProxy는 실제로 서블릿 필터 체인을 관리하는 Spring Security 의 핵심 클래스로, HTTP 요청에 맞는 SecurityFilterChain을 호출하고, 스프링에서 관리되는 SecurityFilterChain을 서블릿 컨테이너에서 관리할 수 있도록 DelegationgFilterProxy로 래핑 시켜 주는 역할을 한다. 그러나 FilterChainProxy는 스프링 애플리케이션 컨텍스트에스 관리되는, 스프링 빈으로 등록되는 클래스로, DelegationgFilterProxy는 스프링 애플리케이션 컨텍스트에 등록된 Security 필터들을 서블릿 필터에 등록해주는 역할을 한다.
👁🗨 Security Filters : 인증, 인가 등의 작업을 수행하는 보안 필터. 스프링 빈으로 등록됨
👁🗨 SecurityFilterChain : 위의 보안 필터들을 구성하는 것으로 필터의 순서와 구성을 정의한다.
👁🗨 DelegatingFilterProxy : 스프링 컨테이너에서 관리되는 SecurityFilterChain을 서블릿 컨테이너에서 관리할 수 있도록 해주는 역할
👁🗨 FilterChainProxy : 보안 필터 관리, 필터 체인 설정, HTTP 요청에 대한 보안 처리
🤍 참고문헌
https://www.elancer.co.kr/blog/view?seq=235
Spring Security란? 사용하는 이유부터 설정 방법까지 알려드립니다! I 이랜서 블로그
홈페이지에 인증 및 권한 기능을 빠르게 부여해 인증 및 권한 보호 기능을 손쉽게 추가할 수 있는 Spring의 프레임워크 중 하나인 ‘Spring Security’에 대해 이랜서에서 자세히 알려드립니다. I spring
www.elancer.co.kr
https://docs.spring.io/spring-security/reference/servlet/
Servlet Applications :: Spring Security
Spring Security integrates with the Servlet Container by using a standard Servlet Filter. This means it works with any application that runs in a Servlet Container. More concretely, you do not need to use Spring in your Servlet-based application to take ad
docs.spring.io
'Study > Java' 카테고리의 다른 글
| Spring Security 적용기 (3) JWT(JSON Web Tokens) 개념 (0) | 2024.04.29 |
|---|---|
| Spring Security 적용기 (2) Spring Security Configuration (0) | 2024.04.25 |
| 기술 면접 준비 5. Java 질문 정리 (1) | 2023.11.18 |
| 기술 면접 준비 4. 자바 변수의 데이터 타입 Primitive type & Reference type (1) | 2023.11.08 |
| 기술 면접 준비 3. 멀티 스레드 (+ 프로세스와 스레드) (0) | 2023.11.07 |



